NATO-compliant intelligence management
ICMT transforms fragmented intelligence processes into a structured digital workflow. Purpose-built for military operations, it ensures intelligence requirements are properly tracked, routed and answered across units and nations – replacing email chains and shared folders with a system that enforces NATO standards at every step.
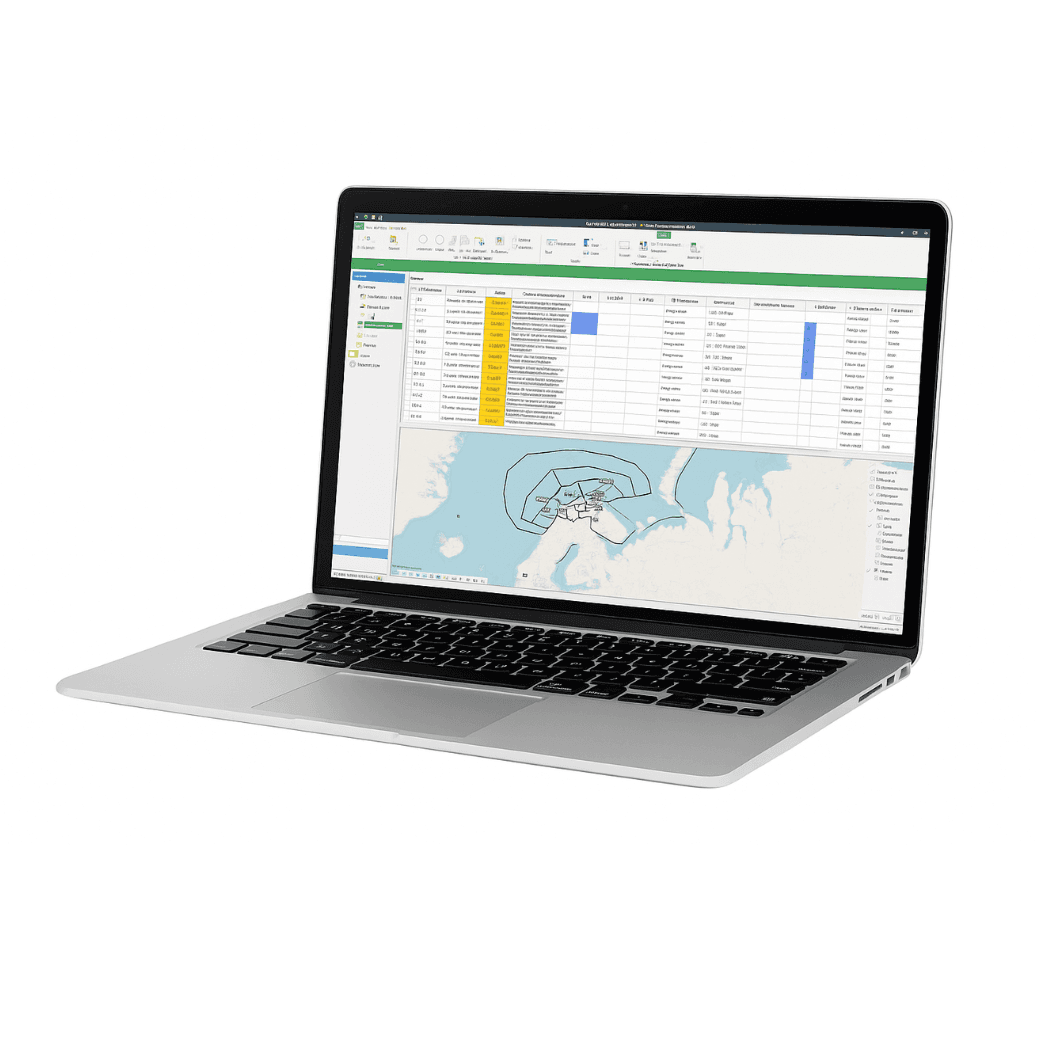
Intelligence Collection Management Tool
Unlike generic tools, ICMT is built on military intelligence doctrine and principles. The system prevents incomplete requests from being submitted, maintains complete traceability of all actions and guides users through the Intelligence Requirements Management and Collection Management (IRM&CM) process.
ICMT builds compliance into the workflow itself – every request follows NATO's STANAG (Standardisation Agreement) protocols, every action is logged, and nothing gets lost in the operational tempo.
From scattered requests to structured intelligence
Military intelligence officers face a critical challenge: ensuring that intelligence requests are not lost, delayed or misinterpreted. Traditional channels, such as email or shared folders, lack structure, traceability, and standardisation – leading to missed deadlines and fragmented situational awareness.
ICMT eliminates these failure points through dedicated intelligence channels and a structured approach. Multi-user collaboration means teams work simultaneously without confusion. Role-based access ensures sensitive requirements stay secure. And full NATO compliance means seamless information exchange with allied forces.
ICMT transforms intelligence management by
Ensuring full NATO compliance
for seamless data exchange across nations and systems
Preventing incomplete requests
from entering the system through enforced validation
Providing full traceability
of all actions throughout the intelligence cycle
Supporting simultaneous collaboration
across multiple users and units
Separating intelligence workflow
from general communication channels
Key features
ICMT isn't just digitising paperwork – it's transforming how military intelligence flows from request to response, ensuring commanders get the information they need to make life-or-death decisions.
Full intelligence cycle support
Covers the entire intelligence process – from defining requirements to tasking sensors and linking collected intelligence back to the original request. This ensures a seamless flow throughout the process, maintaining traceability and reducing manual effort. Reported intelligence is automatically associated with the originating task, giving users a clear operational picture and closing the loop efficiently.
Collection Requirements Management (CRL/CTL)
Streamlines how units manage their intelligence priorities. Units receive Collection Requirements Lists (CRL) from subordinates, prioritise them based on operational needs, then create Collection Task Lists (CTL) for specific time periods. These lists combine internal needs with requirements from other units, ensuring coordinated intelligence efforts across the force.
Structured information exchange (RFI/ISR)
Facilitates the creation, submission, and tracking of Requests for Information (RFI) and Intelligence, Surveillance, and Reconnaissance (ISR) requests in accordance with NATO standards. Every request follows the same format, preventing misunderstandings and ensuring complete information from the start.
Enterprise visibility
Provides insight into intelligence requirements across units, enabling better coordination and situational awareness. This shared view identifies when multiple units need similar information, allowing more efficient use of collection resources.
NATO compliance enforcement
Built to comply with NATO's STANAG AEDP-17 and AEDP-19 standards, ensuring seamless interoperability with allied systems. The system enforces these standards throughout the workflow, preventing non-compliant requests and ensuring reliable international intelligence sharing.
Role-based access and authentication
Integrates seamlessly with Active Directory, allowing users to log in with their existing credentials. Access to information and available actions are then governed by user roles and security clearances, ensuring sensitive intelligence requirements remain protected while enabling necessary collaboration across units.
Our experts
"ICMT gives the intelligence community a structure and compliance to the process that dramatically lessens the workload when followed from top to bottom."
Intelligence Officer, Norwegian Intelligence Regiment
Dig deeper into our solutions
Access detailed product sheets and explore the full scope of our capabilities.